This is How They Tell Me Secureframe Saves the World
A Sponsored Deep Dive on Secureframe: Why SOC 2 & ISO 27001 are Not Boring
Welcome to the 873 newly Not Boring people who have joined us since last Thursday! If you aren’t subscribed, join 41,936 smart, curious folks by subscribing here:
🎧 To get this deep dive straight in your ears: listen here or on Spotify or Apple Podcasts
Today’s Not Boring - the whole thing! - is brought to you by… Secureframe
Secureframe helps companies get enterprise ready by streamlining SOC 2 and ISO 27001 compliance. If you don’t know what that means, I’ll explain. If you do, talk to them:
Hi friends 👋 ,
Happy Thursday!
It’s been a wild week for Not Boring Deep Dive sponsors. Following up on MainStreet’s $60 million Series A a few weeks ago, news came out about two more Deep Divers this week:
Ramp: On Monday, The Information reported that Ramp raised $65 million from D1 and others at a $1.1 billion valuation, followed immediately by $50 million from Stripe at a $1.6 billion valuation. When we did the Ramp Deep Dive in December, they had just raised $30 million.
Pipe: Yesterday, TechCrunch reported that Pipe raised a fresh round of $150 million funding at a $2 billion valuation. When we talked about Pipe in October, they had raised $66 million total.
The bar I use for whether I write a Sponsored Deep Dive on a company is whether I would invest my own money in the company if given the chance (disclosure: I invested a small amount in Ramp, MainStreet, and Pipe after writing about them). You can read more about the Deep Dive selection process here.
Today’s Deep Dive Sponsor, Secureframe is fresh off an $18 million Series A itself. I think that’s just the beginning. They make companies more secure at a time when security has never been more critical, and are competing smartly in a massive market.
(I always tell you how I’m paid for Deep Dives — CPA, CPM, or equity. Today is CPM).
Let’s get to it.
This is How They Tell Me Secureframe Saves the World
Let’s start with a riddle. What do Ukrainian accounting software, Southwest Airlines, and Secureframe have to do with each other?
Any guesses? No? I’ll give you a clue. Secureframe is security compliance software that companies, from 3-person startups to enterprises, use to automate SOC 2 and ISO 27001 compliance, complete audits, and continuously monitor their security. It’s how modern software companies stay safe and compliant with less time, effort, or cost, so they can unlock sales and focus on growing their business.
But what does that have to do with Southwest and Ukraine? Read on to find out.
This is How They Tell Me the World Ends
Remember the old Southwest Airlines commercial in which a bored employee clicks on an email titled “Sick of your job??” and infects her whole office? Wanna get away?
It actually sums up why cybersecurity is so petrifying: all it takes to take down a system is finding and exploiting the weakest link. One employee opening the wrong file can infect an entire company’s network; even worse, in an interconnected world in which every company runs on top of a stack of other companies’ software, one employee ignoring a software update can bring down major companies all around the world.
In This is How They Tell Me the World Ends, New York Times cybersecurity reporter Nicole Perlroth recounts the story of the most damaging cyber attack to date: NotPetya. (Wired tells it here if you don’t want to read the whole book).
On Wednesday June 27, 2017, the day before Ukraine’s Constitution Day, hospitals, banks, ATMs, power plants, the government, and practically all businesses in the country were hit, seemingly simultaneously, with what appeared to be ransomware. It locked computers, deleted files, and spread at breakneck speed from computer to computer, and company to company. Messing with Ukraine on its Constitution Day had become a Russian hacker pastime -- Ukraine’s neighbor routinely shut off the power or deleted files -- but this was different, more vicious. It was also harder to contain.
NotPetya spread via “two exploits working in tandem”: EternalBlue and Mimikatz (technically, Mimikatz is not an exploit but an application used to take advantage of the EternalBlue exploit). EternalBlue was a backdoor into any unpatched Windows computer, and Mimikatz used those computers to steal passwords and break into others. Together, they preyed on the weakest links.
The virus was so hard to contain that it jumped from Ukrainian companies into any company that had an office or even an employee in Ukraine. NotPetya took down systems at: Danish shipping giant Maersk, American pharmaceutical behemoth Merck, FedEx’s European subsidiary TNT Express, and even boomeranged back on Russian state oil company Rosneft. Once the virus was unleashed, there was no stopping it.
And it started by finding a weak link, or more precisely, a weak Linkos.
Linkos Group is a small, family-run Ukrainian software business that makes M.E.Doc, a tax product that’s like a Ukrainian TurboTax or Quicken. Practically anyone who does business in Ukraine uses M.E.Doc. That’s how the Russians got in. According to Wired:
In the spring of 2017, unbeknownst to anyone at Linkos Group, Russian military hackers hijacked the company’s update servers to allow them a hidden back door into the thousands of PCs around the country and the world that have M.E.Doc installed. Then, in June 2017, the saboteurs used that back door to release a piece of malware called NotPetya, their most vicious cyberweapon yet.
All told, NotPetya did over $10 billion in damages, according to a White House assessment. It’s an extreme example, one of the most devastating cyber attacks in history, and a distant one, launched halfway around the world. But the book is chock full of other examples, big and small, of hackers, private and state-sponsored, finding their way into the networks of the largest companies and richest governments.
Cyber is the new global battlefield, but unlike traditional warfare, it’s much harder to contain the impact to specified targets, as NotPetya showed. Now, companies are often casualties of war. They fall victim to civilian and state-sponsored hackers alike.
All of those hackers are constantly looking, or paying, for a way in. They form a global, multi-billion dollar, public-private market for weak links.
How Not To Be the Weak Linkos
OK, did you solve the riddle?
If M.E.Doc and the woman in the Southwest Airlines commercial were Secureframe customers, they wouldn’t have unleashed malware on their co-workers or customers.
Chances are, your company isn’t going to be the weak link in the next NotPetya. But if you’re building a software company of any size, you need to care about security.
In order to sell into enterprises, companies need to prove that they’re secure. After reading the NotPetya story, the reason why should be clear: enterprises can’t afford to let in weak links.
Previously, this prevented smaller companies from selling into larger ones early in their lives. “Bottoms-up” or “product-led” growth is in part a response to slow enterprise sales cycles, which are slow in part due to each enterprise’s bespoke security compliance requirements, which could take months and tens of thousands of dollars to pass, for each company.
Over the past couple of years, though, a standard called SOC 2 has emerged as the de facto security compliance standard. Since SOC 2 is generally accepted as the gold standard, getting SOC 2 certified means that you can sell into large companies much earlier. That’s a huge revenue unlock for young companies. SOC 2, the humble security compliance standard, is partially responsible for sky-high early stage valuations.
Today, most software companies are SOC 2 compliant by the time they hit 20-30 employees, with some even getting it when they’re just three people. In a competitive environment, they can’t afford not to be. If your competitor gets its SOC 2 and you don’t, they have free reign to scoop up large customers while you’re stuck down-market.
But even though SOC 2 (and a host of sector-specific standards like PCI, HIPAA, and FedRAMP) level the playing field by eliminating the need for a new security compliance process for each potential customer, the process is still a massive pain. It takes months, tens of thousands of dollars, and an endless back and forth of screenshots and process documentation with auditors.
Enter Secureframe.
Secureframe makes the whole process faster, cheaper and more effective by integrating with the tools you use to automate the process. Typically, startups spend $25-50k on their SOC 2 compliance process. With Secureframe and all of its automations in place, companies save months of time and 50-70% of the cost of a typical SOC 2 certification.
Luckily, standardization doesn’t just make it easier for companies to get certified and sell into large companies, it also makes it possible for startups like Secureframe to build tools that make the whole process faster, cheaper, more painless, and more effective. To understand why that matters, we’ll cover:
Security Compliance: Important but Not Top Priority
The Compliance Maze
The Value of Standards in the Consumerization of Enterprise
What Secureframe Does
How to Win a Nascent, Massive, Competitive Market
This is How They Tell Me The World Survives
If you want to learn a little something about cybersecurity, standards, and competitive dynamics, come with me.
Security Compliance: Important, but Not Top Priority
Imagine you’re building a B2B SaaS startup, thousands of miles away from Washington, or Moscow. Maybe you’re in Silicon Valley, or Miami.
There are two of you. You have an idea, a couple new M1 MacBook Pros, and cases of Red Bull. You just raised a small pre-seed (what’s that these days, like $5 million?) and IT’S TIME TO BUILD.
It’s easier than ever to build a startup, and harder than ever to stand out. So you mix and match a bunch of off-the-shelf software, plug in Twilio to message customers, Stytch to handle authentication, and Stripe to start taking payments. Security is important to you, obviously, and you read something about NotPetya once, but that’s not the top priority for now. Startups, you’ve read, are all about ruthless prioritization. So you trust that security is important to the companies that build the software on top of which you’re building. With more plug-and-play back-end tech, you’re content to trust (for now, until you have a bigger team). You spend a lot of your time on your points of differentiation, on the front-end -- designing, testing with customers, re-designing, getting feedback, iterating, re-testing. Uh oh! A competitor just got funded -- a $6 million pre-pre-seed! -- and you need to pick up the pace. You hire a couple of engineers, a lead designer, and a salesperson. Something’s working. You have product-market fit! The land grab is ON, and you decide to go upmarket before your competitors do, to start selling to enterprise customers. Everything is moving so fast.
And then it slows down. Because your enterprise customer asked you to respond to an RFP or RFI (Request for Proposal / Information) and to include your security compliance certification. Damn.
The Compliance Maze
Given the potential attackers lurking around every corner, it’s no surprise that large enterprises and even fast-growing startups need to make sure the software they use is secure. That means understanding the software itself, the software that the software is built on, and the processes that the company itself uses to screen employees, manage permissions, and even undertake performance reviews.
Until about a decade ago, each company created its own security compliance hurdles for vendors to jump over. If you wanted to sell into Microsoft, that might mean one set of things, if you wanted to sell into Salesforce, another set of things, and if you wanted to sell into the government, godspeed.
As more software moved to the cloud, the AICPA, one of accounting’s governing bodies in the US, developed the Service Organization Controls (SOC) standards, of which there are three (technically, SOC3 is more of a general use report instead of a full fledged standard). SOC 2 is really the only one you need to care about.
While an accounting-governing-body-created set of system and organization controls sounds tedious, and it is, it’s also way better than going through a new bespoke process for each potential customer. Instead, you can get your SOC 2 certification and proudly display that on your site and in RFI/RFPs to prove that you’re a trustworthy vendor. SOC 2 tells potential customers that you probably won’t, accidentally or intentionally, give hackers an open door into their networks, or into their customers’ networks.
The AICPA created SOC 2 in 2011, and has iterated on it a few times. After the last iteration in 2017-2018, SOC 2 became the de facto industry standard. SOC 2 is now table stakes. By the time a company hits 20-30 people, they’ve likely gotten their SOC 2 compliance. Many get it when the company is just the co-founders and a few laptops. That’s because not only do large customers require that their vendors have SOC 2, but that their vendors’ vendors have SOC 2. It’s SOC 2 all the way down.
Getting SOC 2 certified requires companies to do a bunch of things. According to WorkOS, those include:
Quality oversight of the company as a whole (performance reviews, independent voices, background checks, etc.)
The SDLC (software development lifecycle) is transparent, trackable, and controlled (issue tracking, unit testing, version control, etc.)
Your application and underlying infrastructure are secure and monitored (encryption, logging, APM, vulnerability scans, etc.)
You’ve implemented access controls for internal services and SaaS (de-provisioning accounts, 2FA, malware detection, etc.)
A lot of these things are best practices anyway; SOC 2 just makes you prove and document everything. First, startups typically get SOC 2 Type I, which is just a snapshot in time, and then get SOC 2 Type II, which is audited over 3-12 months, to satisfy customers’ compliance requirements. Plus, they need to get recertified annually, all signed off on by an auditor.
And that’s just SOC 2. There’s also ISO 27001, published jointly by the International Organization for Standardisation and the International Electrotechnical Commission, which was recently revised in 2013. ISO 27001 has ~75-85% overlap with SOC 2, but adds on a few information security-specific requirements.
If you deal with credit cards, there’s Payment Card Industry (PCI) Standards. Healthcare has the Health Insurance Portability and Accountability Act (HIPAA). The Federal government has the Federal Risk and Authorization Management Program (FedRAMP), which is so onerous -- it takes about two years and $1 million to complete -- that less than 300 vendors are FedRAMP certified. The Department of Defense recently introduced the Cybersecurity Maturity Model Certification (CMMC), its attempt to make it easier and more accessible to sell software to federal agencies. The average CMMC audit costs $10-30k instead of $1 million.
All of that sounds like a ton of work, and it is. It all sounds bad and overly onerous, but it’s not. Standards actually level the playing field and make it possible for companies to sell into enterprises and other startups more quickly and cheaply than ever before.
The Value of Standards in Consumerization of Enterprise
Since the last iteration of SOC 2, it’s become the de facto security compliance certification. That doesn’t mean that all of a sudden, companies who never required any security compliance now require SOC 2 from their vendors; it means that all of the companies that had created their own compliance requirements began accepting SOC 2 instead. SOC 2 is a lot like the Common App in college admissions: do it once, use it in many places, sometimes with a little supplemental work required for specific schools / enterprises.
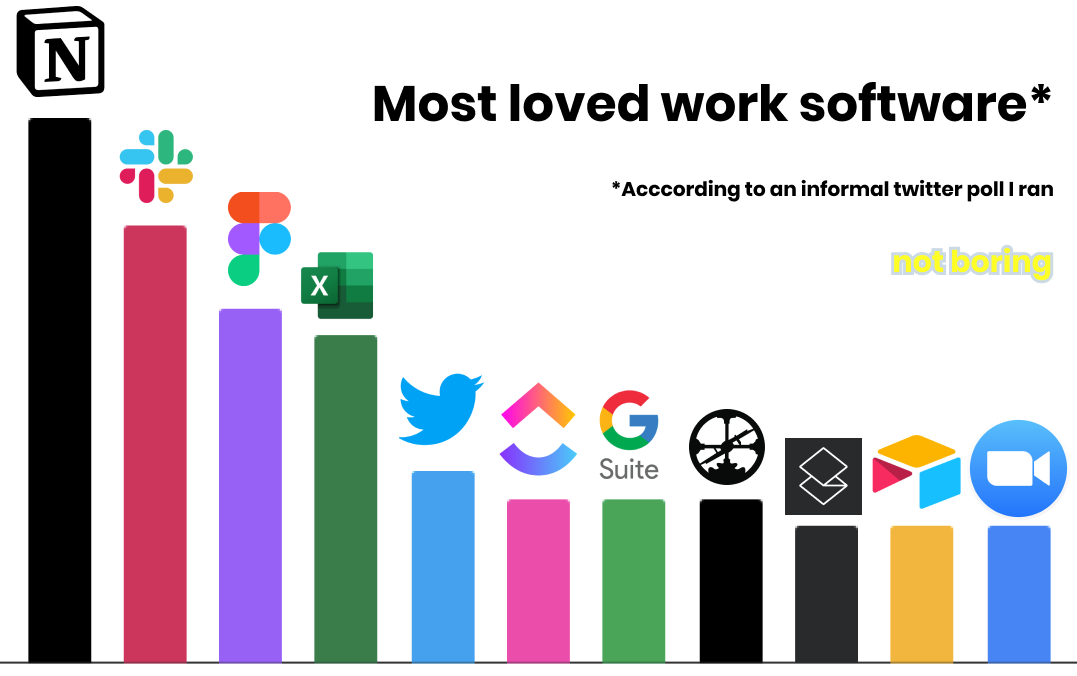
That makes it dramatically easier for small companies to sell into bigger ones. And increasingly, bigger ones are open to that. The “consumerization of the enterprise” refers to the idea that companies are full of people who use smooth, well-designed software in their personal lives, and have come to expect the same at work. In Bill-A-Bear, I highlighted a list of the work software people on Twitter told me they loved the most. With the exception of Excel (which is a whole ‘nother story), all of peoples’ favorites are modern, smooth, consumer-like.
No one wants to use shitty software all day, and new software is often easier-to-use than old software (people typically build new software startups to replace old, shitty software), but at the same time, enterprises and startups alike need to maintain their procurement standards. If startups want to sell into enterprises earlier, it’s on them to be enterprise-ready sooner.
SOC 2 makes that possible more cheaply and easily than was previously possible (as do ISO 27001, CMMC, and the rest). That means that startups are able to land bigger clients, earlier. Much Substack ink has been spilled over high early-stage startup valuations, but some of the valuation increase can be explained by the fact that companies are landing bigger clients at a stage at which they previously would have been limited to selling into other startups.
That said, getting compliant is still a painful process. SOC 2 and ISO 27001 mean that you only need to go through one painful process per year, but it can still take tens of thousands of dollars and many months of manual back-and-forth with auditors to get certified.
That’s where Secureframe comes in.
What Secureframe Does
Secureframe helps companies get compliant in weeks rather than months, typically saving customers an average of 50% on their audit costs (which can traditionally run over $50k). Founded by Shrav Mehta and Natasja Nielsen in 2020, Secureframe integrates with over 40 of the most commonly used products companies use to automatically understand their security posture and automate an increasing amount of the security compliance certification process.
Maintaining a SOC 2 gets more complex over time. As Secureframe highlights, “Every new contractor, employee, customer, and vendor requires more security controls.” Growth is great, but it makes compliance messier.
That’s why Secureframe is focused on automating as much of the process as possible.
If companies plug in their HR system like Gusto or Justworks, Secureframe knows when a new employee joins.
By connecting to a company’s device management software, like JAMF, Fleetsmith or AirWatch, Secureframe can ensure that devices are secure and accounts are properly controlled.
Integrating with cloud providers like AWS, Google Cloud, or Azure gives Secureframe insight into the security of a company’s infrastructure.
Instead of asking employees to regularly screenshot their workflows and emailing them to auditors every week, Secureframe does as much as possible automatically, and provides auditors with detailed reports.
There’s still a lot of manual work in the process, which may hamper Secureframe’s ability to scale efficiently -- some because Secureframe needs to hire more engineers and build more integrations, and some because parts of the process are structurally manual. For example, you can’t pull board meeting minutes with a direct integration, but Secureframe lets customers easily upload them instead. The team is hiring aggressively to automate the process as much as possible, and already features three times as many integrations as competitors like Vanta.
The approach seems to be working. Secureframe has hundreds of clients and has grown nearly 20x in the past year. Just a couple of weeks ago, it announced an $18 million Series A, led by Kleiner Perkins with participation from Base10 Partners, Gradient Ventures, Soma Capital, and others, just five months after its $4.5 million Seed round co-led by Gradient and Base10, with participation from Soma Capital, BoxGroup, Village Global, Soma Capital, Liquid2, Chapter One, Worklife Ventures, and Backend Capital.
Secureframe’s business model is straightforward: it’s a SaaS business, with pricing based on company size and the certifications a company wants to get. Once it wins a customer, it’s incredibly sticky. Setting up all of those integrations takes upfront work, and as long as Secureframe makes the SOC 2 and ISO 27001 processes faster and smoother, companies are unlikely to churn. Quite the opposite, actually: Secureframe should see strong Net Dollar Retention, meaning that each customer spends more every year, for a few reasons:
Companies need to recertify every year. In order to continue to sell to large companies, they need to remain compliant, which means they need Secureframe.
As companies grow, they pay Secureframe more money.
Secureframe will add new standards like PCI, HIPAA, and CMMC, which have overlapping requirements with SOC 2 and ISO 27001. It makes sense to use the same company for all of them.
More security compliance certifications means more potential customers for Secureframe’s customers. One of their investors told me that “the thesis around Secureframe has revolved around them ‘enabling a new generation of enterprise software companies.’" Clients like Hasura, Instabase, and Fabric rely on Secureframe to get SOC 2 and ISO 27001 compliant earlier so that they can begin selling to large companies, and to maintain their certifications over time.
But Secureframe isn’t alone in the security compliance space. How it plans to win is a lesson for other companies in competitive, non-winner-take-all markets.
How to Win a Nascent, Massive, Competitive Market
The security compliance market is massive. Just 3-4 years into its life as the gold standard, about 40,000 companies get SOC 2 alone every year, at an average cost of $25,000-$50,000. That’s $1-2 billion per year, not counting ISO 27001, PCI, HIPAA, FedRAMP, CMMC, or any number of other security compliance certifications. Secureframe and its competitors believe that as they bring down the cost and effort required to get certified, they’ll expand the market.
Secureframe isn’t the only company that noticed. Companies like Vanta, Laika, and Tugboat Logic also streamline security compliance.
Plus, security compliance software is incredibly sticky, not just for Secureframe, but for its competitors. As long as it works as advertised, customers will stick around and grow. That means there’s urgency to win customers early.
What do you do to compete and win in this kind of market?
First, you build a differentiated product with a superior customer experience. This is the most important part. Secureframe is a relatively new entrant, but it’s the fastest-growing and best-funded for a reason. Secureframe stands out from competitors on a few key dimensions:
In-House Compliance. Head of Compliance was the company’s first hire, and Secureframe has one of the industry's only in-house compliance teams to make sure that customers aren't just checking the box; they're actually secure and implementing the best security practices. There's no worse customer experience than being hacked after you paid to be safe.
End-to-End Support. Head of Customer Success was one of the first five hires. Secureframe works with clients all the way through certification, even once they’ve handed off the process to auditors, and is committed to a smooth customer experience in a space where “smooth” isn’t a thing.
Most Integrations. Secureframe’s industry-leading 40+ integrations (3x as many as Vanta) means less manual work for customers, faster turnaround times, and ongoing systems monitoring.
Agentless. Secureframe uses an Agentless approach to get access to customers’ data. Some competitors have customers install agents on their devices, which can be time consuming, difficult to set up, and less secure. You want a security compliance company that’s the most… secure.
Second, you grow really fast and acquire as many customers as possible. This is why Secureframe is sponsoring Not Boring today. It’s also why I keep hearing about SOC 2 on my favorite podcasts. When I hit play on Invest Like the Best, Patrick is there singing Vanta’s praises, and when I switch over to 20 Minute VC, Harry’s doing the same for Secureframe.
It’s a good old fashioned land grab. Agreement on new standards unleashed a new market, and the rush is on to win customers. Every customer that Secureframe wins is a customer that a competitor can’t.
(If you’re reading this, you’re on Team Secureframe. That’s the rule. Go sign up!)
Secureframe has raised more money than any of its competitors, despite being a newer entrant. Capital isn’t a moat in and of itself, but it can certainly help in a space in which speed is key.
Shrav told me about a few other really clever things that Secureframe does to acquire customers, but he swore me to secrecy (for now) because he doesn’t want the competition to pick up his tricks.
Third, you build in switching costs so that customers don’t leave once you’ve acquired them. Secureframe does this in two ways:
Integrations. Integrations create a better customer experience; they also dig moats. Once a company integrates all of their tools, and everything’s running smoothly, they’re less likely to leave and go do it again with a competitor. Soon, Secureframe will open up an integration marketplace so that the companies coming to them today saying, “We want to build an integration with Tool X” can do it, and open up the integration to other Secureframe customers. This requires being the biggest (see: point 2, grow really fast) so that it’s worth it for companies to build integrations on your platform. If they pull it off, it will give Secureframe platform network effects, like Windows or the App Store.
Vendor Management. One of the challenges with security compliance is that you don’t just need to prove that you’re secure, but that the vendors you use are secure too. It’s all about minimizing weak links. Since a 100 person company uses 50 vendors on average, this process can be a huge headache. Secureframe works with companies to find and upload all of their vendors’ security compliance certifications, and is building the largest database of vendor security information. In the future, if one company uses AWS and uploads their compliance certifications, the next company that comes in can just pull that off the shelf, saving time and money.
Next, you add more compliance certifications. Secureframe is using its fresh funding to grow beyond SOC 2 and ISO 27001 into PCI, HIPAA, FedRAMP, HITRUST, CMMC and beyond. More certifications can be a deciding factor when comparing Secureframe versus its competitors upfront, and can be a reason for companies to switch from one platform to another despite high switching costs.
Since it’s mainly a software business with most costs going to engineering, sales, and customer success, Secureframe has massive margins. It can spend to acquire customers, and spend on R&D to make sure that it has the products it needs to keep them happy and grow their business. Secureframe isn’t constrained by capital, it’s constrained by its ability to hire and execute.
And it doesn’t need to win the whole market. With market dynamics like these, competition can actually be a good thing. The industry only coalesced around SOC 2 as the standard a few years ago, and the competitors are sharing the cost and effort of getting the word out. I was more receptive to Secureframe after hearing a Vanta ad, and likewise, potential customers might be more receptive to Vanta after hearing a Secureframe ad (or reading this piece) (but seriously, use Secureframe).
Ultimately, though, what it’s really about is making companies, and the internet broadly, more secure. The biggest risk to any competitor, including Secureframe, is that one of its customers gets breached. It’s a reputational landmine, and given the interconnectedness of the system, a potential security threat to many customers.
That’s why Secureframe is building more than a “check the box” product. It’s great that SOC 2 lets companies sell to more customers, but the real goal is to actually secure them.
This is How They Tell Me the World Survives
Secureframe’s mission is to secure the internet and help businesses trust their vendors. If Secureframe is maximally successful, there won’t be another NotPetya.
Today, that means making it as easy as possible for customers to get their SOC 2 and ISO 27001 certifications. Plus, its compliance team already provides recommendations on best practices that go beyond certifications. Tomorrow, it’s adding more certifications. But certifications meet the basic requirements, and Secureframe thinks that there’s so much more companies can do to secure themselves and their customers.
As Secureframe reviews more vendors and assesses their risk, it can help all its customers better manage their own risk. It can recommend vendors based not just on their certifications, but on what Secureframe knows about their security practices more broadly. And as each new vendor comes on, Secureframe can automate and speed up the process for everyone else.
Beyond that, Secureframe is working towards building its own standard, drawing best practices from existing standards and from the vendors and customers that work with Secureframe. Combining its own standard with the world’s largest database would give Secureframe the holy grail: the ability to set a higher bar that actually makes the internet secure and make the bar easier, faster, and cheaper to clear so that companies can focus on what they do best.
SOC 2 compliance… not as boring as it sounds, huh?
If you want to learn more about getting compliant and securing your business, schedule a call with the Secureframe team.
Don’t be the weakest link. Goodbye.
Thanks to Shrav for telling me the Secureframe story, Anant at Soma for the great insights, and Dan and Puja for editing.
How did you like this week’s Not Boring? Your feedback helps me make this great.
Loved | Great | Good | Meh | Bad
Thanks for reading and see you on Monday,
Packy











Can you dive into a deeper anaylsis?