Evervault: Encrypt Everything
Encrypt the Web. End Data Breaches. Build a Massive, Multi-Product Business.
Welcome to the 532 newly Not Boring people who have joined us since last Monday (woah)! If you haven’t subscribed, join 114,143 smart, curious folks by subscribing here:
🎧 Instead of an audio edition today, subscribe on Spotify or Apple Podcasts to get my interview with Evervault CEO Shane Curran tomorrow.
Hi friends 👋 ,
Happy Thursday!
One of my favorite things about technology is that it turns humanity’s biggest problems into opportunities for entrepreneurs. The market does a pretty great job of rewarding extraordinary people for fixing things for the rest of us, so much so that some of those people have enough money to buy Twitter.
Data breaches are one such problem, and ending them is one such opportunity. That’s what Evervault is trying to do by giving developers simple, powerful tools to encrypt the web. If Evervault succeeds, its prize will be one of the most valuable positions in the internet stack.
This is a Sponsored Deep Dive. You can read about my selection process and conflicts here; the most important takeaway is that I only write about companies I would invest in, find fascinating, and think you should know about. If you don’t already, you should certainly know Shane Curran and Evervault.
Plus, as Shane pointed out below, when companies pay a little more, they put more effort into implementation. I hadn’t quite thought of it that way, but I think that we’re able to get better access and more interesting insights because these are sponsored.
Let’s get to it.
Evervault: Encrypt Everything
8. Don’t Hinder the Builder.
Privacy is a basic expectation and human right, but it’s something that should never create any friction or slow down the speed of technological advancement.
– Evervault, The Encryption Manifesto
For the past three years, the Chief Technology Officer of the world’s fifth largest company by market cap and largest cloud provider has worn the same t-shirt whenever he speaks at conferences:
Dr. Werner Vogels, Amazon’s CTO since 2005, has a catchphrase to go along with the fashion: “Dance like no one is watching; encrypt like everyone is. Encrypt everything.”
“Encryption is the tool we have to make sure that no one else has access to your data,” he tells audiences and employees alike.
You deal with encrypted data every minute of every day. Whenever you send a text message, for example, it’s encrypted on the way out of your phone and decrypted at the other end. Crypto runs on public-key cryptography – your wallet uses your seed phrase to derive your private key to sign transactions.
To oversimplify it, encryption takes readable data and turns it into gobbledygook that no one can read except the people who have the keys. Take my Social Security Number, which is 294-36-1652. (JK, good try) But take that SSN. Often, if I enter it somewhere online, like in a credit card application, it’s stored in plaintext data, just like that, “294-36-1652”, in a database. The database may be encrypted using Data at Rest Encryption, but if someone is able to hack into the database, or simply access it with their credentials, they’ve hit the jackpot. My SSN and all of the information in there is theirs for the taking.
This isn’t a hypothetical. In 2019, an Amazon engineer, Paige Thompson, used her permissions to hack into Capital One’s AWS server and steal data from more than 100 million Capital One customers, including 140,000 Social Security Numbers (SSN) and 80,000 bank account numbers.
In the ideal state, what would have happened is that Thompson would have hacked in, and instead of plaintext SSNs, would have seen 140,000 random text strings that look like this:
ev:Tk9D:in0+WDhHs2cpetd/:AqaGHmNI8XCxO0S9pAQDusU+rwf6WpIrM9wM0xbAXYFM:fKKWClDvNK4sY9K7Nff6nMSUKasc9zet4UrGpA==:$But Capital One used database encryption, not field-level encryption, which would have meant that even someone with access to the database couldn’t have accessed the data inside in plaintext. And that’s Capital One, a $54 billion public company that spends a lot of money and human power on security. Most companies are far less prepared, and data breaches are becoming far more common.
According to the Identity Theft Resource Center, there were a record-breaking 1,862 data breaches in 2021, up 68% from 1,108 in 2020 and 24% higher than the previous record of 1,506 in 2017. In 83% of data breaches, hackers got access to peoples’ Social Security Numbers.
If you want to really feel what’s at stake, I recommend that you read Nicole Perlroth’s excellent book, This is How They Tell Me the World Ends or listen to her interview on Lex Fridman Podcast:
The stakes are high, and they’re getting higher as more of our lives, data, reputation, and wealth move online.
That’s why Vogels wants you to Encrypt Everything. Evervault wants to help.
“When a company encrypts with Evervault, they could put their database on a billboard and no one could get at the data,” Shane Curran, Evervault’s 22-year-old founder and CEO told me.
I’ve been following Evervault for over a year. In last summer’s Zero Knowledge, which I co-wrote with Jill Gunter, we described its value proposition and approach:
The ideas underlying Evervault aren’t new. Public-key cryptography traces back to the 1970s with Ralph Merkle’s (yes, Merkle of Merkle Tree fame) 1974 paper Secure Communications Over Insecure Channels. Since Satoshi published the Bitcoin Whitepaper in 2008, so much money and talent has flooded the historically wonky academic field of cryptography that cryptographers are solving very hard problems faster than ever before. Cryptography is somehow cool.
And yet… there were a record number of data breaches in 2021. Big companies are still storing data in plaintext. Companies spend billions of dollars becoming PCI-, HIPAA-, ISO-, SOC2-, GDPR-, and CCPA-compliant, while leaving big honeypots of user data in their databases.
That’s what Evervault wants to fix. Its Encryption Manifesto is very clear:
Evervault is building encryption infrastructure for developers. Our mission is to encrypt the web. Our goal is to end data breaches.
Evervault is making two big bets:
Centralized control of private keys in trusted, secure environments will remain important. Even once everything is decentralized, you’ll still need a safe place to store your seed phrase or private keys.
Abstracting and simplifying the process of encryption for developers is the right approach to encrypt the web. This is the classic API playbook – like Twilio did for telecom, AWS did for servers, and Stripe did for payments, Evervault wants to make it extremely simple for “developers [to] build encrypted apps where data is encrypted at all times, and can still be processed.”
Most people care about data privacy, but not enough to actually do anything about it. Certainly, all else equal, users would rather have their data be more private than less. All else equal, companies and developers would rather build encrypted products that allow them to process data without storing it.
So Evervault needs to make all else equal. They need to:
Encrypt the Web
Without creating friction or slowing down technological advancement
While matching the developer experience of building without encryption.
Or as Shane put it: “We need to build things that are trusted by the ultimate cynics on Hacker News but that are super simple to use, the best encryption with the best developer experience.”
That’s a lot harder than it sounds, but Evervault seems as well-positioned as anyone to pull it off. Today, we’ll cover why, how, and what happens if they succeed:
Shane and the Irish Mafia
How Evervault Works
Opinionated Use Cases
The Ultimate Cynics on Hacker News
Evervault’s Next Decade
This is a lesson in both encryption and company-building. If Evervault succeeds, they’ll not only make the web a safer place, but will wedge themselves into a crucial position in the world’s tech stack, a place from which both they and third-party developers can launch new products only possible in a world of verifiably private data.
But first things first, the encryption. When it comes to protecting your sensitive personal data, you want someone preternaturally gifted on your side. Meet Shane Curran.
Shane and the Irish Mafia
Shane Curran was six-years-old when he first installed Linux. He was seven when he started coding in Visual Basic and created a basic web browser that anyone could download online. By age 11, he’d built peoplez.info, an online database of names and email addresses. And the next year, he built Libramatic, a cloud-based library management system that let librarians catalog books more easily.
The Irish Times, which I’ve learned writes the best headlines, titled this one:
And here is the Chief Executive (12) in question:
Librarians actually used Libramatic, and they stored “all this secret data” like names and email addresses and passwords in there, which Shane realized was a little terrifying, because, well, a 12-year-old built that app. A 12-year-old with no particular expertise in data security.
So young Shane Curran decided to do what no 12-year-old I’ve ever met would have decided to do and take up an academic interest in cryptography. He first entered the BT Young Scientist competition, the longest-running science competition in the world, the next year. He lost in 2014, 2015, and again in 2016.
In 2017, at the ripe age of sixteen, he entered with a project called qCrypt. As The Irish Times wrote in a piece called How a Dublin teenager is helping you bring your secrets to the grave, Shane’s project aimed to answer these questions:
If you have a secret and wish to keep it a secret until your death, how do you guarantee its cryptographic integrity until that time, especially with computing advances that could make today’s state-of-the-art encryption crackable? And how do you enable the secret to be released, but only after death?
The fourth time was a charm. Shane won the competition.
The win brought a lot of commercial interest. The next morning, there were twenty or thirty emails in his inbox from companies who wanted to use the technology he’d built.
So young Shane Curran decided to do what no 16-year-old I’ve ever met would have decided to do and set to work figuring out how to commercialize his game-changing post-quantum cryptographic product.
A year later, in 2018, he launched Evervault. He explained it by way of analogy: Stripe for data privacy.
Which is to be expected, because any company that lets developers [do some historically hard thing] in just two lines of code with clean documentation compares itself to Stripe. The payments company, founded by Irish brothers Patrick and John Collison in 2010, is a gold standard in Silicon Valley and was recently valued at $95 billion, with secondary shares trading hands as high as $152 billion according to Pitchbook.
But Evervault has a more direct claim to the Stripe lineage than most. Twelve years before Shane, Patrick was named BT Young Scientist 2005, at the age of sixteen, for his project, Croma: a new dialect of LISP.
So when Shane was thinking about turning his science project into a real startup, he called on Patrick and a group of Irish founders in San Francisco.
As he explained at a 2020 event, “During the Easter break before the Leaving Cert, I hopped on a plane over to San Francisco and just decided to meet with the ‘Irish mafia’ over there, who were all extremely helpful.”

The trips paid off. According to Pitchbook, Evervault raised a $3.2 million Seed from Sequoia and Kleiner Perkins in October 2019. You can actually see the deck they used here.
Half a year later, in May 2020, Evervault raised a $16 million Series A from Index Ventures.
That’s a lot of money to give a then-20-year-old, but it’s not hard to see why they did it.
Shane is a force. At the earliest stages, a company is always a bet on a founder, and Shane is the right mix of wildly talented and calmly mature that investors like to back. He’s built a strong engineering-heavy team capable of pulling off something very hard.
And Evervault is riding the right wave: GDPR, CCPA, and an alphabet soup of regulations and compliance regimes, combined with the rise of crypto, mean that there is a massive opportunity for the Stripe of data privacy, the company that can make it easy to comply with regulations and keep private data safe. As a comp, Very Good Security (VGS), founded in 2015 to attack the sensitive information problem with tokenization instead of encryption, was last valued at $550 million in February 2021.
So the team is there and the market is there. It’s going to come down to execution and product. So how does Evervault work?
How Evervault Works
Before we dive into Evervault’s product, allow me to make the obvious caveat that I’m not an engineer or a cryptographer or even that smart. I’m going to do my best to explain what Evervault does, and how, based on everything I’ve read, conversations, and a little hands-on experience in Replit 👀
Here goes.
In an August 2021 blog post titled Encrypting the Web, data encryption company Evervault provided a simple thought exercise to prove that all developers will inevitably build encrypted apps:
If developers have a choice between building apps with plaintext data and building apps with encrypted data — assuming the developer experience is matched — they’ll choose to build encrypted apps every time.
The “assuming the developer experience is matched” is doing a lot of work.
Let’s assume that all else equal, the web should be encrypted. Personal information would be safer and data breaches would be far less common. It’s such an obvious point that the question isn’t whether or not the web should be encrypted, but, if encryption is so obviously good, why it hasn’t been already.
Evervault’s bet is that it comes down to the developer experience. Shane believes that if developers can integrate best-in-class encryption in a few lines of code, instead of needing to dedicate months and hundreds of thousands of dollars to it, it will move up the priority list.
Evervault’s challenge is that it needs to do a bunch of really hard things behind the scenes and deliver them in a way that’s simple to integrate and doesn’t hurt the performance of its customers’ sites. Like Batman, it needs to keep users safe without them really knowing about it.
To do that, Evervault has architected a system with three different levels:
The foundation of everything is the Evervault Encryption Engine (E3). If you want to go really deep on E3, Evervault wrote a technical but approachable piece called How We Built the Evervault Encryption Engine (E3).
Evervault’s design requirements give the clearest sense for what E3 is intended to do:
Evervault must verifiably not be able to access or decrypt data;
E3 should be use-case agnostic;
E3 must have low latency, high throughput, and full redundancy; and
The integrity of keys must be absolutely guaranteed.
Ultimately, E3 should be able to perform cryptography on any arbitrary data without Evervault being to access it, and allow apps to process the data inside as quickly as if they weren’t encrypting and decrypting it. And no matter what, Evervault cannot lose your keys.
All encryption and decryption happen inside of E3, which lives inside of AWS Nitro Enclaves, “isolated, hardened, and highly constrained virtual machines (EC2 instances).” Evervault was the first company to get a product deployed on AWS Nitro Enclaves after switching from original plans to use Intel SGX.
The AWS Nitro Enclave is a Trusted Execution Environment (TEE), similar to the Secure Enclave where your iPhone keeps sensitive data like biometrics separate from everything else, and disconnected from the cloud. Apple can’t access your biometric data even if compelled by the government; it needs your password or biometrics to use your private key into the Enclave. Similarly, neither Evervault nor Amazon should be able to access your data in a Nitro Enclave. (See the E3 post for more technical discussion).
Essentially, when you trust Evervault with your data, what you need to trust are AWS Nitro Enclaves and the fact that Evervault integrated correctly, which we’ll touch on below.
Evervault built E3 first, and everything that they’ve built since, and will likely build in the future, will be built on top of E3.
Third-party developers never interact directly with E3. Instead, they go through Relay, Cages, or Inputs by incorporating Evervault’s SDK and changing a DNS record (essentially pointing the website through Evervault, the same way websites integrate Cloudflare).
Relay is the first developer-facing product Evervault built on top of E3. In Evervault’s How We Built Relay post, they explained that Relay is “an abstraction layer over the Evervault Encryption Engine (E3), designed to make it simple to begin encrypting your most sensitive data before it reaches your server.”
Companies could, and some large companies do, work directly with AWS Nitro Enclaves or other chip-based TEEs, but doing so can mean hiring dedicated (and expensive) security engineers, spending months integrating, and dealing with ongoing maintenance.
Most developers can plug in Relay in five minutes to do most of what’s needed: automatically encrypt data at the field level before it hits their database, where the information is stored as hashes. When a user needs the data, Relay decrypts it on the way out. Like so:
But what if Evervault gets hacked? Here’s an incredibly important point:
Evervault’s clients store encrypted data, but not private keys.
Evervault stores private keys, but not encrypted data.
In that way, if a hacker hacked either Evervault or one of its clients, it would end up with piles of worthless hashes. In order to steal real private information, they would have to successfully hack both Evervault and a client at the exact same time, which is theoretically possible but exponentially less likely.
Even with all of the world’s best cryptography, though, Evervault is only as good as it is simple. The whole bet is that developers will choose encryption if it’s practically as easy as not encrypting.
A good test for that might be… whether my dumb ass is able to encrypt data with Evervault.
And the answer is yes!
In its docs, Evervault has a Tutorial that uses Not Boring favorite Replit to build a Relay-encrypted form in minutes.
When I enter my phone number in the Evervault-less site, it returns this in Replit:
No bueno! That’s my full telephone number, right there in plaintext 🤮 for anyone to steal.
When I enter a couple lines of javascript, though…
…and tell Evervault to encrypt the “phone” field when I hit “submit”...
…the phone field goes through Relay and all I see in the Replit console is this:
Good luck calling me at that number!
There’s no better way to learn than to get your hands dirty. I highly recommend going through the Tutorial and spinning up a Repl if you’ve heard the word “encryption” a lot but want to know what it feels like in your fingers. I’m just showing you this one piece, but it also shows you how to set up a Cage, send an SMS, and set up a Relay mTLS.
So Relay is essentially a simple blind pipe between a developer’s form and E3, where it gets encrypted on the way into a database and decrypted on the way out, simply and quickly.
Relay is the simple product that pretty much any developer who touches personal information probably can and should just integrate today. Shane called it “the 80/20 version of the product,” the version that works well enough for most people.
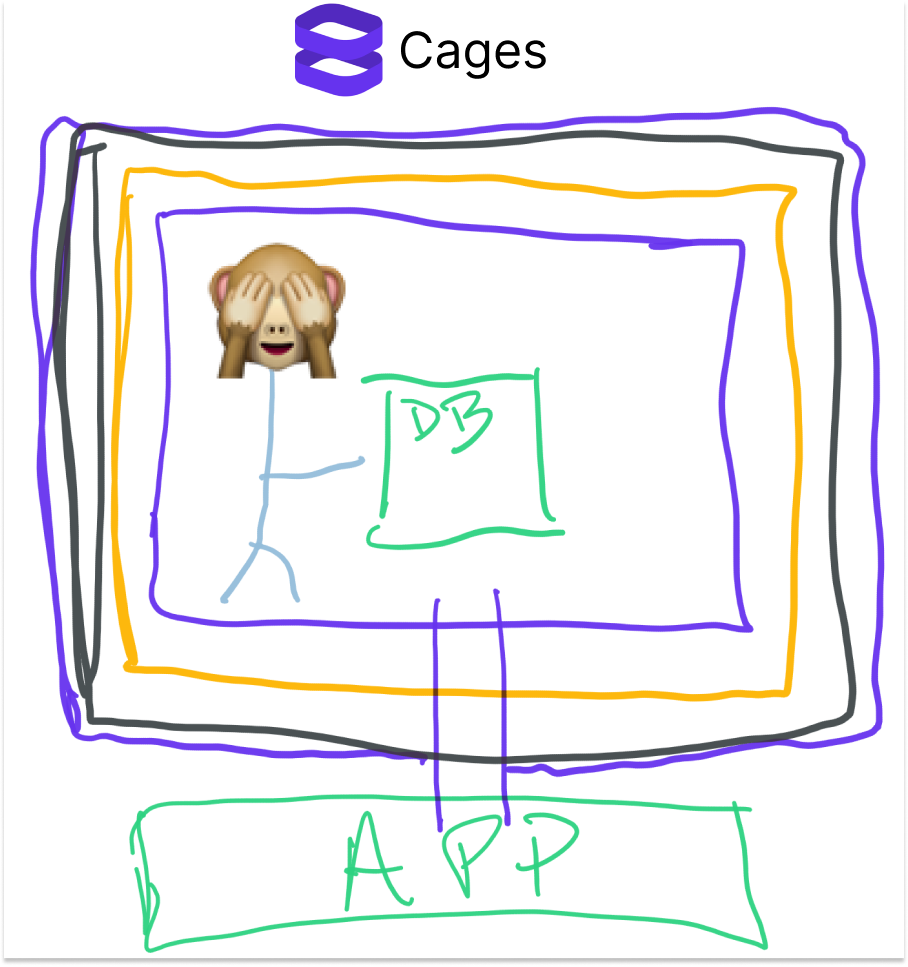
But some companies and developers need to do more with sensitive data than just keep it safe. They need to process the data, use it to feed models, send them to third-parties via API, and more. Most of the reasons that “data is the new oil” involve actually doing something with the data. For those use cases, Evervault built Cages. Here’s how they describe it in the docs:
Cages are serverless functions hosted on Evervault for processing the data you encrypt with Relay or our SDKs. You can use Cages to isolate your Node.js code that processes sensitive data from the rest of your stack.
That likely means something to an engineer, not as much to me. What it reminds me of is those quantum physics thought experiments like Schrodinger’s Cat in which something happens inside of a box but you have no way of knowing what it is from the outside. But this time, there’s a blind scientist running experiments inside. As soon as the experiment is finished, he sends the answer out, and then the Cage is destroyed.
A more typical use case might be running a machine learning model that needs to use sensitive data, like personal health information. The Cage can unencrypt the data, the model ingests and runs on it, and then shares the results outside of the Cage.
Both Relay and Cages eliminate the trade-off between Encrypt Everything and the inexorable march towards more data usage. Odds are that we will put more of our data online – and likely be compensated for its use – not less, and that companies will build both great and terrifying things using it. Like DALL-E 2 but based on your recent transactions. Evervault’s existence means that they can do so more safely, without accidentally leaking personal or sensitive information in the process.
E3, Relay, and Cages all fit the E3 design principle of being use-case agnostic. They’re the infrastructural pieces of the product, on top of which companies and Evervalt itself can build.
And over the past couple of months, with the infrastructure in place, they’ve started doing just that.
Opinionated Use Cases
Evervault started, quite literally, as a science fair project. The first few years of its life were about proving that the infrastructure could actually be built in a way that works for companies – from small startups to large banks and healthcare companies.
Now, with working and battle-tested infrastructure, Evervault is spending some of its time focused on go-to-market. In other words, they need to show prospective customers how Evervault might work for their specific need. Sometimes, the best way to speed up market adoption is to dive in and show the way:

In one example, Shane told me that as they were talking to financial institutions, a few potential customers came to them and asked whether Evervault takes them out of scope for PCI DSS Compliance. If you haven’t spent much time in fintech, PCI DSS stands for Payment Card Industry Data Security Standard. It’s a set of guidelines mandated by the credit card companies to make sure companies who collect credit card data are keeping it safe, which is a good thing, but a pain to comply with. According to ControlCase, there are 12 things that companies need to do to be PCI DSS Compliant:
So Evervault “did a little Googling, and it turns out, the answer was yes.” Evervault keeps payment data so safe that, with a few lines of code, companies can reduce their scope to the simplest form (SAQ-A for you fintech and compliance nerds), saving a ton of time, money, and pain. So Evervault hired someone to run the Compliance business, and last week, they rolled out Evervault Inputs.
Inputs builds on E3 and Evervault’s existing SDKs, and makes it dead simple for customers to collect credit card info securely and compliantly. That makes it a lot easier for companies that collect card information to picture how they might use Evervault – which is sometimes hard to do with infrastructure – and makes the sales process easier.
In our conversation on Not Boring Founders (dropping tomorrow), Shane told me this product “took off. It means you kind of start to build momentum in isolation via a very high-performing, interesting business” and build new products easily on top of sturdy existing infrastructure.
Evervault built another such new product for crypto – not cryptography, the web3 one that we usually talk about here.
In February, Evervault rolled out its first consumer-facing product out of the Evervault Encryption Lab: 121824.
So named because seed phrases, which give users access to their non-custodial crypto wallets, are typically either 12, 18, or 24 words, the product lets users encrypt and access their seed phrase in a product Evervault built on top of Relay. Even in a fully decentralized world, seed phrases are a point of failure. People write them on pieces of paper and lose them, or cut them up and scatter them across the globe like Horcruxes. When people lose their seed phrases, they irrevocably lose access to their assets. It’s one of the many reasons some people stick with custodial wallets.
Instead, with 12:18:24, users enter their seed phrases, and Evervault encrypts them at the field level. To access them, Evervault makes users use magic links and SMS authentication instead of passwords, because as we know from Stytch: Kill the Password, passwords are a security nightmare. Theoretically, it gives hardware-grade security with the convenience of software.
The product is a first glimpse at how Evervault might interact with web3. Coincidentally, Cages work on the same elliptic curve as bitcoin. Under the hood, a lot of the cryptography is similar, just applied differently.
It’s unlikely that Evervault will roll out its own wallets anytime soon, though. Instead, 12:18:24 is an attempt to show developers what they might be able to build on top of Evervault.
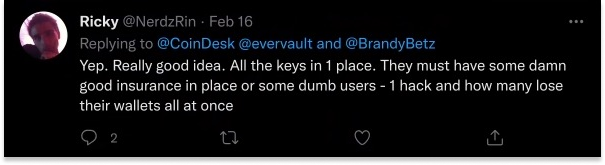
Exposing the product to consumers also shows the communications battle that Evervault has ahead of it. When Coindesk tweeted its article on the launch, one twitter user replied:
This is the challenge with launching a technically sophisticated product, especially one that deals with privacy and security. It’s similar to the challenge that Worldcoin faces convincing users that it doesn’t store their eye images. The truth – the actual security of the product – is the most important thing, but perception is a pretty close second.
Shane knew that coming into it. That’s why he said he wanted to build something simple to use that could be trusted by the ultimate cynics on Hacker News.
The Ultimate Cynics on Hacker News
Hacker News, Y Combinator’s news forum, is one of the most cynical places on the internet. As Byrne Hobart wrote in his excellent piece on Stripe:
One of the rituals people go through whenever a tech company hits a valuation milestone is to go back and look at the first thread about the company on Hacker News. Dropbox, as we all know, could be built in a weekend—doesn't everyone know how rsync works? Since Coinbase was looking for a cofounder when Bitcoin was down, it was obviously an attempt to pump the price back up to $25.
Convincing the ultimate cynics on Hacker News is about as high a bar as a company can attempt to jump in tech, for two reasons:
There are so many smart, technically-savvy people there that they’ll sniff out any potential errors, flaws, weaknesses, or contradictions.
They get even snarkier than is technically called for in packs.
I think Hacker News’ special charm is that it’s full of all of the smartest people who still qualify as, or behave like, midwits:
Evervault hasn’t won all of Hacker News over yet. When Shane posted How We Built the Evervault Encryption Engine (E3) eight months ago, he got a fair amount of very good questions (and some “well, ackshually” replies):
The good news is, instead of me pretending to be more technical or cynical than I am, the dialogue on Hacker News provides a good picture of the questions and concerns at play. You can dive in here and here.
What impressed me most is the way that Shane interacted with all of the commenters. He’s about 30x more mature and measured than I would have been, acknowledging the validity of peoples’ concerns and addressing the specific points one-by-one with real depth.
When I asked him which of the critiques were most valid, he told me that ultimately, you do need to trust AWS Nitro Enclaves, down to how tightly they manage their entire supply chain to ensure that no one is able to put exploits in the chips they use.
Over time, Evervault’s dream is to be able to use homomorphic encryption, which would allow it to run calculations on the encrypted data itself without needing to trust a Trusted Execution Environment, but for now, the technology isn’t ready for commercial use. “It’s wonderful technology, it’s just impractical at scale and for large datasets because it’s super slow,” Shane explained.
That thoughtfulness and honesty is one of the many little examples throughout my time getting to know Shane that gave me confidence that Evervault would remain at the cutting edge, but not pretend to be further ahead than it is. Another is the fact that the company has a page on its site dedicated to all of “the most important cryptography papers.” It’s shades of Stripe with a clear focus on attracting the kind of people who appreciate a good cryptography paper.
There’s a deep respect for the difficulty of the challenge, an excitement around the opportunity to package and commercialize the most cutting-edge tech in the simplest way, and a humility about the fact that the best they can do today is not the best there will ever be, which is expressed both in words and in the product’s modular architecture.
If homomorphic encryption, zero knowledge proofs, or a fully decentralized, trustless system ends up being more secure than its current approaches in the future, Evervault will plug those methods in and focus on abstracting away the complexity and commercializing cutting-edge cryptography.
Because Evervault isn’t building any one specific product as much as it’s building a delivery mechanism through which to inject security into the web in a bunch of different ways.
Evervault’s Next Decade
“Evervault is all of these sort of independently interesting businesses, but as a company, it really only comes together in years nine and ten,” Shane predicts, “When you have all of these really sort of cohesive, comprehensive products that finally kind of snap together like a LEGO house or something.”
He mentioned partnering with cyber insurance companies to insure against attacks as one possible extension, and products like PCI-focused Inputs and crypto-focused 12:18:24 provide breadcrumbs as to where all of this might go. But while Shane is coy about the full suite, there’s one comp that might hint at Evervault’s ambitions: Cloudflare.
Cloudflare started with a wedge in the cybersecurity space, too, providing DDoS-mitigation services. They realized that not only did they stop attacks, but the sites that used Cloudflare actually ran faster. They quickly became a Content Delivery Network (CDN), the business that they’re most well-known for today.
Importantly, Cloudflare uses a similar process to set up its CDN to the one that Evervault uses to integrate “in 5 minutes by including our SDK and changing a DNS record.” Because everything flows through Cloudflare, they’ve been able to roll out, and cross-sell, an enormous amount of security- and performance-related products:
If you squint, Evervault might be targeting a similar goal by finding its way into the same position through a new developer population. In How we built Relay, Evervault wrote, “The ultimate aim for Relay is to be as broadly distributed as the best in class CDN providers like Akamai, Fastly, and Cloudflare.”
Cloudflare today is a $40 billion company after tumbling nearly 50% from a November 2021 peak. Having the world’s websites point to you is a good place to be in the stack.
From there, can Evervault build the Cloudflare of the encrypted internet?
From that perspective, the decisions that it’s making today make sense. It faces competition from Open Source projects, like Solid, created by Tim Berners-Lee, the guy who invented the World Wide Web. While Solid might attract the more hardcore security developers today, Evervault is going after the huge percentage of normal developers who aren’t thinking about security but should be and with the younger startups that just want to focus on their core product. There are many more of them than there are security experts.
Even today, there are signs of Evervault’s long-term plans in the business model. To build the Cloudflare of the encrypted internet, they need to prioritize long-term usage and market share over short-term revenue maximization.
As they explained in the Seed Deck, they have a Heroku-like usage-based model that means that they grow as their customers grow, like many API-first businesses do:
This is a business model designed for a product gets in with companies early and grows with them as they grow, as Stripe, Twilio, Vercel, and other API-first companies successfully have.
While generating revenue is important in the short-term, the main metric the company looks at is total amount of data encrypted. Counterintuitively, Shane told me they’ve actually found that if they charge people a little bit more, it pushes them to integrate the product more quickly and makes them value the integration more. The fact that, for now, charging more leads to faster usage is a positive quirk.
That metric is important for a couple of reasons, one global and one local:
Globally, the more data Evervault encrypts, the less susceptible the web is to data breaches, and the closer Evervault is to its goal.
Locally, the more data Evervault encrypts, the more of the internet’s activity there is moving through Evervault and the more opportunity it has to add and cross-sell products as part of its suite of data privacy-first products.
An encrypted web is both safer for companies and users, and better business for whichever company developers most trust to encrypt their data, process their encrypted data, and decrypt their data.
Evervault is still early in the journey. Shane said that, as it stands – E3, Relay, Cages, Inputs – “we have sort of one or two rooms in the Lego house, but building the whole thing and having it come together is still a long time away.”
It’s a big, ambitious goal and a lot needs to go right. Even more importantly, one key thing can’t go wrong: Evervault is built on trust; any data breaches would be devastating. But the prize if they can pull it off is enormous and important.
While he acknowledges that focusing on the short-term while building towards that complete Lego house long-term is the most challenging part of his job, Evervault is willing to take the time to build the foundation the right way, so that it can ultimately build secure products on top at high-velocity. As fellow BT Young Scientist Patrick Collison said:
There’s something quite deep about the notion of using time horizons as a competitive advantage, in that you’re simply willing to wait longer than other people and you have an organization that is thusly oriented.
Put another way, give Shane enough time and Evervault might hold all the keys.
Thanks to Dan for editing, and to Shane and the Evervault team for working with me!
If you enjoyed reading about Evervault and want more, subscribe to Not Boring Founders on Spotify or Apple Podcasts to get my interview with Shane tomorrow.
Thanks for reading, and see you on Monday,
Packy































auspicious digits btw